-
Notifications
You must be signed in to change notification settings - Fork 8.2k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Fix: Canvas socket auth #24094
Fix: Canvas socket auth #24094
Conversation
23eb0e0
to
87f25fa
Compare
87f25fa
to
6af2f2e
Compare
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
LGTM! I confirmed that we don't get authorization errors on any of the functions that query elasticsearch while logged into a user, so this does indeed fix #23303.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
This is definitely better than the previous situation. The one side-effect which we'll have to figure out is how this should work with auth providers which use short-lived tokens which need to be refreshed. When we run authenticate directly, or indirectly via server.inject there's potential for us to be using the refresh token to get a new access token, which should be returned to the end-user with the set-cookie header, which we end up ignoring. This currently impacts SAML, but more and more auth providers will be switching to using these tokens, and this will definitely become exacerbated at that point.
|
Also, my LGTM is conditional on CI going green. |
|
@kobelb would you mind opening a new issue about refreshing tokens? It's certainly something we should figure out for GA. |
6af2f2e
to
8c0be93
Compare
💚 Build Succeeded |
|
6.x fe7c9ec |
## Summary Closes #23303 ~(@cqliu1 can you confirm this too?)~ confirmed Fixes the way we capture the request info when configuring the socket and providing it to plugins via `callWithRequest`. Instead of exposing a route that returns the info, simply use the request object that comes back from `server.inject`. Also adds a check in the `elasticsearchClient` handler exposed to plugins to ensure the session is still valid because using `callWithRequest`. 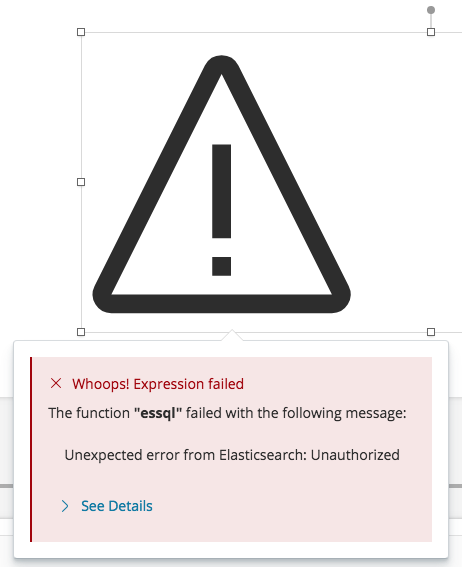 *Note:* the actual error message is a bit different, but this is how the failure is exposed to the user

Summary
Closes #23303
(@cqliu1 can you confirm this too?)confirmedFixes the way we capture the request info when configuring the socket and providing it to plugins via
callWithRequest. Instead of exposing a route that returns the info, simply use the request object that comes back fromserver.inject.Also adds a check in the
elasticsearchClienthandler exposed to plugins to ensure the session is still valid because usingcallWithRequest.Note: the actual error message is a bit different, but this is how the failure is exposed to the user